- cross-posted to:
- privacy@lemmy.ml
- technology@beehaw.org
- cross-posted to:
- privacy@lemmy.ml
- technology@beehaw.org
It seems like the sensitive information is being logged by the app or iOS. The article says that “devices’ encrypted logs” were cracked. That info shouldn’t be logged at all to begin with. There are similar open source apps for peer to peer communication. In an open source app this kind of issue would have been recognised easily. But knowing Apple this was probably an intentional backdoor.
The Bloomberg article cited (https://www.bloomberg.com/news/articles/2024-01-09/china-says-cracked-apple-s-airdrop-to-identify-message-sources or https://archive.is/XnvO8) once again doesn’t mention the relevant institute by name, but here’s the Chinese article from Beijing Municipal Bureau of Justice: 2024-01-08 司法鉴定:司法鉴定揭开“隔空投送”匿名传输的神秘面纱 https://sfj.beijing.gov.cn/sfj/sfdt/ywdt82/flfw93/436331732/index.html
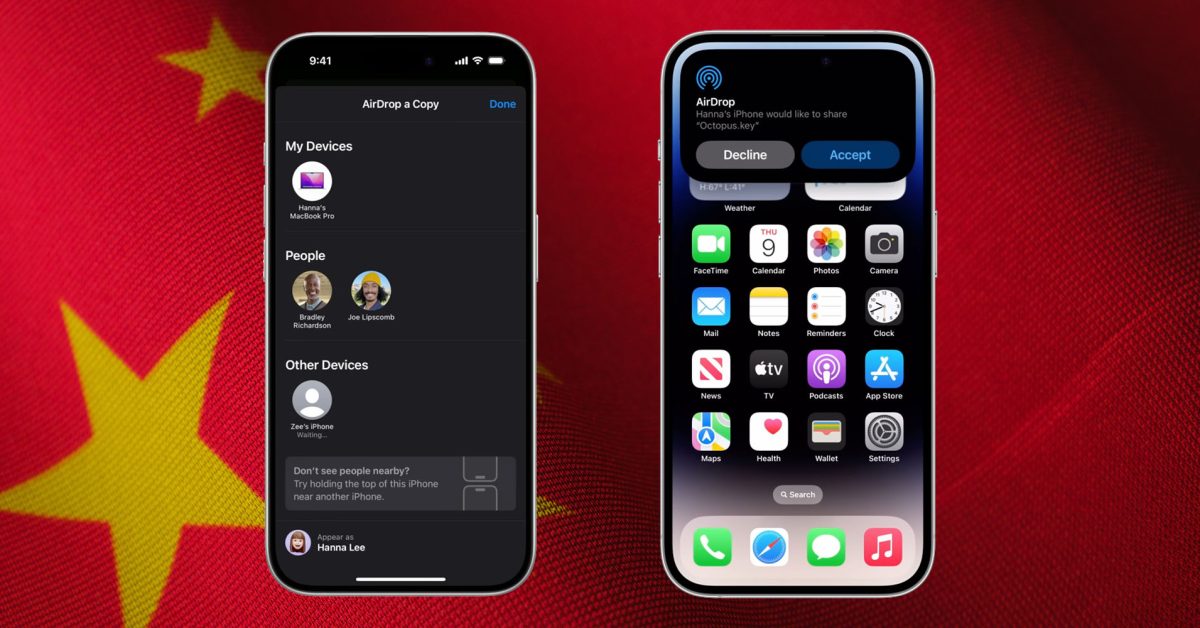
This paragraph reveals how they found out the AirDrop sender’s email and phone number:
北京网神洞鉴司法鉴定所的司法鉴定技术专家们通过深度解析iPhone设备日志,明确传输原理,找出了与AirDrop 相关的记录。经检验发现发送者的设备名、邮箱和手机号相关字段,其中手机号与邮箱相关字段是以哈希值的形式记录,且哈希值部分字段被隐藏。为实现快速破解该字段,技术团队制作了一张详尽的手机号与邮箱账号“彩虹表 ”,能够将密文转换成原始文本,快速锁定发送者的手机号与邮箱账号。
Basically the sender’s phone number and email addresses were stored as hash values, but the hashes were just partial values. The judicial appraisal institute “北京网神洞鉴” created rainbow tables (precomputed table for caching the outputs of a cryptographic hash function, usually for cracking password hashes) to bruteforce the information.
As Chinese mobile numbers follow certain formats (11 digits, starts with 1, known list of prefixes etc.) it is probably very easy to generate a rainbow table for this. Though the article doesn’t mention if the phone numbers and email had separate hash values so this is just one way to do it.
From Apple’s “AirDrop security” page we can see that this matches up: https://support.apple.com/guide/security/airdrop-security-sec2261183f4/web
AirDrop uses iCloud services to help users authenticate. When a user signs in to iCloud, a 2048-bit RSA identity is stored on the device, and when the user turns on AirDrop, an AirDrop short identity hash is created based on the email addresses and phone numbers associated with the user’s Apple ID.
When a user chooses AirDrop as the method for sharing an item, the sending device emits an AirDrop signal over BLE that includes the user’s AirDrop short identity hash. Other Apple devices that are awake, in close proximity, and have AirDrop turned on, detect the signal and respond using peer-to-peer Wi-Fi, so that the sending device can discover the identity of any responding devices.
This article is about the AirDrop receiver finding out the sender’s information, but doesn’t mention if the reverse is possible. But if we look at the same AirDrop security page, it is probable that in AirDrop “Everyone mode” an attacker could find out the information of Apple devices around them:
In Contacts Only mode, the received AirDrop short identity hash is compared with hashes of people in the receiving device’s Contacts app. If a match is found, the receiving device responds over peer-to-peer Wi-Fi with its identity information. If there is no match, the device doesn’t respond.
In Everyone mode, the same overall process is used. However, the receiving device responds even if there is no match in the device’s Contacts app.
For people using Apple devices or even other brands, especially in the US, take caution as this is a finding one Chinese local government published, who knows how many vectors of attack the US intelligence agencies is aware of.
Great run down of the mechanics behind this.
Apple hype proven to be bullshit once again. Hope to see a repeat of this https://www.nytimes.com/2017/05/20/world/asia/china-cia-spies-espionage.html